
Phishing attacks are some of the most widespread and common fraud attacks that happen on the internet. According to Proofpoint, 75% of global organisations experienced some kind of phishing attack in the past year, making it one of the most important forms of cybercrime to protect against.
What is phishing?
Phishing attacks are attempts to gain access to sensitive data or information, like usernames, credit card numbers, social security details, or passwords, by pretending to be official communication from a trusted or frequently-used services, such as Paypal, mail-services or banks.
How does phishing work?
Phishing relies on people being distracted and not really paying close attention to the fine details of what portal they’re sending their sensitive information on. A phishing attack uses a fake website that looks close enough to the original website that they won’t immediately notice the differences between the fake website and the real one, a little bit like being unable to tell a high-end clothing brand from a cheap knock-off unless you’re really familiar with all the details. Unlike a knock-off bag, a fake website can siphon off enough of your information to really create problems for you down the line.
Why are phishing attacks effective?
With so much of our lives now online or requiring online access, it’s easy to get caught up in a phishing attack as the methods that are primarily used – random emails, chatting on an instant chat messenger, and texting codes – have now become something mundane and every day, especially during the pandemic when so much business is conducted online. What’s one more email asking you to input your Paypal password, or a chat from a friend urging you to sign up for another free account? And would you really notice if ‘Netflix’ was spelled differently to how it normally is on a website that looks, feels, and operates the same as the Netflix website?
Phishing is effective because it catches people off-guard. By the time you realise that a website or chat message isn’t from a trusted source, it’s already too late: whoever has access to your information can do whatever they want with it.
Usually, what they want to do with it is gain access to even more of your information, and potentially your money.
What are the types of phishing attacks?
Phishing can take several forms, but these are the most common:
Email phishing is the most common, and some of the most sophisticated phishing attacks have been conducted over email. There are four main types of email phishing attacks:
‘Bulk’ phishing is a mass attack sent out to numerous targets, and doesn’t tend to be personalised or targeted. Attackers will normally masquerade as banks, streaming services, and cloud productivity providers, and use the information gained through the attack for money, or to steal sensitive information from within the targeted organisation.
‘Spear phishing’, on the other hand, is a targeted phishing attack and usually includes the use of tailored emails. This kind of attack takes planning, as usually the attackers need some personal information about their target to successfully pull off an attack. These attacks are usually aimed at executives or people who work in finance, such as audit firms and accountancy.
‘Whaling’ specifically targets high-profile executives, again with information that’s normally of interest to the target, such as a customer complaint that they would really like not to escalate to their boss.
A smaller, much less frequent offshoot of whaling, is CEO fraud. By pretending to be a senior-level executive, attackers can convince other employees that they need to perform a specific action, such as wiring money to a different account. This has a much lower success rate than other forms of phishing,
Finally, there’s ‘clone phishing’ — and you might have already heard of this one! Clone phishing is when a legitimate email you’ve received before gets copied wholesale. The link that was in it gets replaced with a malicious link containing a virus. This tends to happen only if the user has been hacked before.
Voice phishing
While phishing emails are the most common, there’s other forms of phishing to be concerned about. Attackers will target multiple people at once, and claim that there’s been dubious activity on their bank account, and to call a number that’s close enough to the real bank’s number not to raise awareness. From there, the panicking victim is coaxed to reveal sensitive account information to ‘resolve’ the fraud. The rest plays out just as you’d expect.
SMS phishing
This is a new one! With the rise of smartphones comes the rise of SMS phishing techniques. They’re virtually identical to email phishing, but they replace the use of email messages with SMS messages. You get a message that asks you to click a link, call a phone number, or contact an email address, and you’re sent to another webpage that asks you to enter your credentials, and that’s all, folks! With smartphone browsers being compacted, it actually makes it more difficult to identify a legitimate website from a fake website, as the window is too small to analyse it properly, which means a lot more people get taken advantage of than they normally would be.
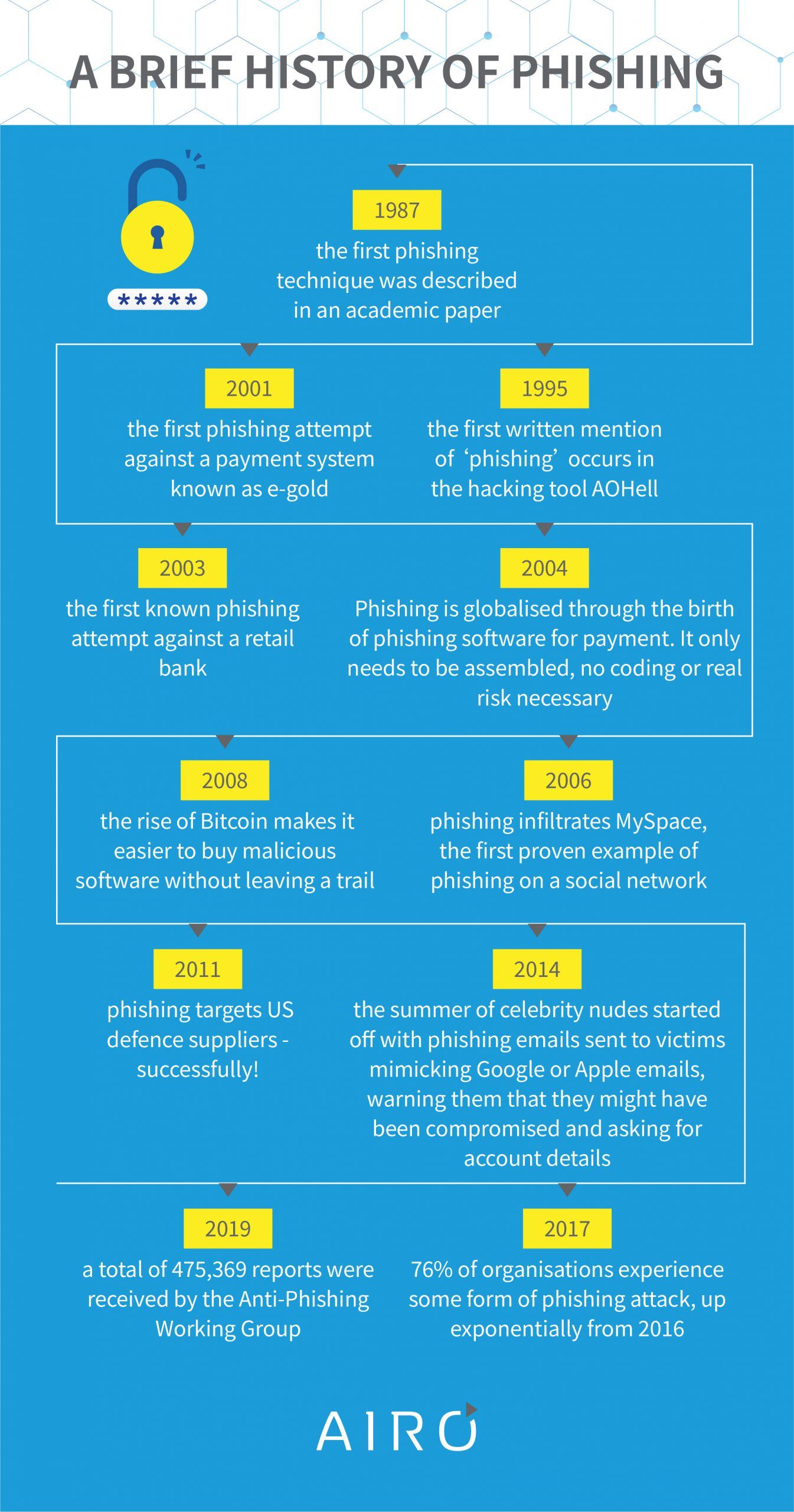
How can you prevent phishing attacks?
These statistics and figures might make it look difficult to prevent phishing attacks, but it’s actually really easy! It just takes a little bit of time, effort, and focus.
- Always look at the spelling.
Most phishing emails or texts will have typos and errors in the content, or more subtly, the domain name will be different. Double-check that it’s the right service, for example: amazon.com instead of amazonstore.co.uk, or something similar.
- Question everything.
If it’s to renew a subscription or ask you to take action, ask yourself why you’re receiving this email to begin with. Services like Paypal, Amazon, and Netflix aren’t going to message you randomly; there’ll be a purpose to it, like someone trying to access your account or an update on a show you’re watching. If the email came out of nowhere, the chances are that it’s not a legitimate email, and you’re better off without answering it!
- Enable 2FA.
Two-factor authentication is one of the best methods of dealing with phishing attacks. By enabling two factor authentication, your account isn’t just protected by a password and a username, but also by your smartphone, something that is physically impossible for hackers to gain access to. Even if your password is exposed, all it really means is that you need to change your password.
- Create a password management policy.
The best password management policy is a working password management policy. It might be tempting to stick to one password that’s easy to remember for multiple accounts, but for maximum safety, what you should do is change your password frequently, and have an independent password for each account. This can help reduce the risk of plenty of hacking attacks, not just phishing!
- Education is key.
Understanding why phishing is a problem is a good way of making sure that your employees understand the importance of not clicking on unverified links or answering emails they’re not entirely sure the source of. When in doubt, make the time to educate your employees, and yourself – it’ll pay off in the long run!
- Take a phishing test
We’ve can help you protect your business at the root: by teaching your employees the hard way how easy it is to get phished. While your employees might be doing their best to keep your protected, phishing can be convincing to the most tech-savvy employee, which is why running a simulation lets you find your weaknesses before a cybersecurity threat does.
The test is completely free and comes with a training module to help you teach your employees better cyber practices. If you’re interested, just fill out the form at the end of this post.
Conclusion
Although it seems difficult to run a business online nowadays and to mitigate all the security risks available online, it’s actually easier than you think! Most businesses can outsource their digital security to companies created to take care of everything from password management policies to remote working. If you think you could benefit from outsourcing security, we’d be happy to advise you on what would work best for you.

Human error is the leading cause of cybersecurity threats to corporations. See how well-prepared your employees are and run a simulated phishing attack to make sure your employees know exactly how to spot a scam.
Here’s how it works:
- available for up to 100 users.
- customisable language selection, landing page, and test templates.
- identifiable red flags and explanations.
- PDF emailed within 24 hours with phish-prone %
- rank your organisation against others in your industry

